Everyone’s raving about Evernote these days – and with good reason, since from my brief experience with it the UI is great, indexing works very well indeed and it’s fast.
Plus it’s multi-platform (although not all features work the same way on all platforms) and the Windows version can run in “portable” mode from a USB stick, which makes it tremendously appealing to me (I have it installed inside a TrueCrypt volume in my corporate laptop).
The thing is, despite this largish post on Evernote’s site regarding security, I’m not really sure I’ll be using its syncing features – at least not for now.
You see, when I was reading that post I thought this passage was slightly odd:
When you add a note to the service, it is secured like your email would be at a high-end email provider. This means that your notes are stored in a private, locked cage at a guarded data center that can only be accessed by a small number of Evernote operations personnel. Administrative maintenance on these servers can only be performed through secure, encrypted communications by the same set of people. All network access to these servers is similarly protected by a set of firewalls and hardened servers. Your login information is only transmitted to the servers in encrypted form over SSL, and your passwords are not directly stored on any of our systems.
Emphasis mine, of course.
But, you see, I thought it very odd that SSL was only mentioned for password transfer, so I decided to dig up a packet analyzer and submit Evernote to what I like to call the iDisk test – i.e., verify if the data is transmitted securely or not.
Why? Well, I am the sort of person who, knowing that data transmission security is an end-to-end affair, uses SSL for everything, from IMAP to Google Reader. Security is not just about authentication and making sure your passwords are safe. It’s also about making sure your data is safe, whether or not it’s stored in a secure vault1.
And that includes using “high-end email providers” such as, erm, .Mac and Google Apps For Your Domain.
Which, in fact, provide me with secure end-to-end transmission of data over SSL, and where I currently store my stuff2 via IMAP.
What many people don’t seem to realize when designing online services these days is that it is a trivial endeavor for anyone to sniff out your stuff from the air in a public Wi-Fi hotspot.
Plus the internet runs through a lot of strange places (like hotel and college networks), so I like to know how my data is transmitted, no matter how inconsequential it happens to be.
So I fired up Evernote and created a simple note:
I then fired up a packet sniffer and hit the sync button. I had no trouble finding my note among the captured packets:
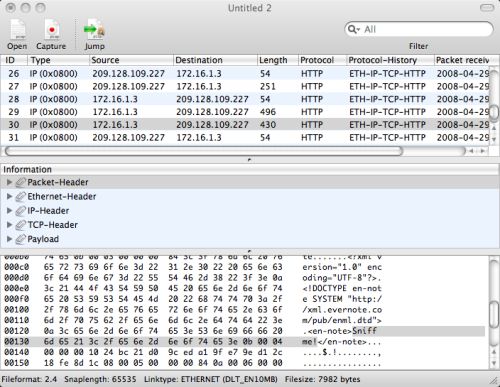
This can be reproduced by anyone in, oh, around 5 minutes or so (go and grab CPA, it’s simple and straightforward to use). Sniffing other people’s packets is left as an (unethical and unadvisable) exercise to the reader.
It is true that Evernote logs in (and apparently does a bit more) over SSL, but for some reason it falls back to plain, unfettered (and quite readable) HTTP to transmit your data to their servers.
Which might be understandable for performance reasons, but which is regrettable in a service that aims to help you store and manage your information across multiple machines.
Maybe this will get fixed after the preview (it’s nothing that a few SSL accelerator cards can’t solve), but until then, and despite its brilliance in other regards, I have to rate Evernote it a D- security-wise.
—
1 And even then I’d only consider the storage truly secure if it was encrypted as well, but that’s another matter – I accept that decrypting stuff from disk on the fly isn’t everyone’s cup of tea.
2 Interested parties may want to pick up MailArchive, clean it up a bit, and make it store stuff via IMAP and SSL – Spotlight will index the results just fine, although not with the same style and panache as Evernote. And for extra brownie points, build a Cocoa text editor that stores its stuff directly into IMAP